Reusable KYC: when a dedication to decentralization self-sabotages
Are we our own worst enemy?

Covering systems thinking and context, agency, hard borders, trust, trust triangles, and governance.

No two people can share an exact understanding of anything deep and meaningful simply because we each have different contexts. Conversation relies upon and can never wholly substitute for context. Nevertheless, we can work to grow a shared understanding through conversation, and the relationship between conversationalists evolves in the process.
The relationship is immanent in such informational exchange[1].
On one level, the opening paragraph here pertains to this being a blog post about conversations I’ve valued in recent months. But there’s another level given that ‘digital identity’ is our subject. Identity, in what you might call the natural and non-bureaucratic sense, is reciprocally defining and co-constitutive with relationships and information exchange[2].
Identities are immanent in the relationships immanent in information exchange.
Conversation — both synchronous and asynchronous — is an art I haven’t mastered, as my colleagues at the AKASHA Foundation will attest! I remain but a keen student. Fortunately, as far as the topic of ‘digital identity’ goes, I have found two deep domain experts with sufficient patience and, it seems to me, a shared love of conversation in the form of Doc Searls and Drummond Reed.
In light of the conversations, Doc, Drummond, and I will have subconsciously updated our understanding of the others, i.e. the role the others play in the internal narratives we each maintain to help us make sense of the world. Importantly, we update our contextual understanding of ourselves in this storyline too; or more accurately, we update one of our selves. And sometimes a variant self is spawned, and now and then one fades with irrelevance.
Our identities, our selves, are formed through internal narratives. The internal narrative is informed by the interactions. And the interactions are modulated by the identities.[3] Social, reciprocal, concurrent, and forever in flux. One might describe the whole thing as essentially human; so much so that we hardly think about it.
This post addresses aspects of ‘digital identity’ we’ve explored together in recent months, at the prompt of Doc and Joyce Searls last October in response to the SSI dystopia critique. It represents my contributions to and my reflections on our dialogue unless otherwise stated, and it serves as much to continue the conversation as log it, and loop others in too.
The post isn’t intended to reflect the presentation that I needed from Doc or Drummond, or that I thought they needed from me. This is now a different context, the context of pursuing shared understanding across the ‘digital identity’ community more broadly.
Per the December post logging a conversation with Phil Windley, I will bring the threads together under appropriate subject headings, but in this case the copy isn’t necessarily verbatim and it isn’t presented dialogically. Here are those subject headings:
But before we dive in, let me (re)invite you to my context.
Per the definition of generative identity, I entreat you to consider architectures and designs for ‘digital identity’ in terms of their consequences for psychological, sociological, and ecological health — self, culture, and nature — rather than, say, the ease with which a hotel room might be reserved, or some general enhancements to process efficiency or veracity. Developing innovative capabilities to such ends has value, no doubt, including in humanitarian contexts, but if it harms the self, culture, and nature in the process, it will amount to an appalling step backwards rather than an enlightening step forwards.
Cause-and-effect thinking dominates. One eats because one feels hungry. One runs because the wolf looks hungry. This has served us wonderfully well in combination with our highly-evolved social mechanisms for cooperation[4].
Development of systems thinking emerged as it became increasingly obvious through practice that many of the problems we’re interested in nowadays are better approached and understood in the context of relationships rather than in isolation[5], entailing a shift from a mechanistic to an ecological worldview[6]. We wanted heat and power and so we mined and burned coal. Today, the ecological worldview directs us instead towards renewable energy sources.
While everything is ultimately connected to everything else, the universe does not of course represent a suitable system of study in most instances! Systems thinking requires some conscious distinction between those entities and relationships that come within the scope of concern and those that can be considered more tertiary by practical assessment, even though a system is not just a supersystem (i.e. containing subsystems) but also a subsystem (i.e. a part of a supersystem). The systems thinker always dedicates some cognitive cycles keeping such delineations under constant review.
Three months after the original critique of self-sovereign identity (SSI) in 2019, and more precisely after the resistance to it, it occurred to me that the miscommunication and confusion might be attributed to different system scopes. Perhaps that should have dawned on me earlier. These most recent conversations have confirmed for me that the ‘digital identity’ community continues on the whole to work within one system scope while I advocate and work within a larger system scope.
My reference to larger there should not be mistaken to mean superior just by dint of size. As I’ve noted, one’s selection of system scope is based on reasoning and judgement as to what should be taken into account versus what can be left out. And as I wrote at the time[7]:
I think there may be a growing recognition that the problem space is wider and deeper than SSI’s arbitrary delimiters may have it. There are too many examples of human action dedicated to ‘solving’ for one aspect of an ecology only to fuck up the health of the ecology. We cannot afford to fuck up because our subject is human dignity, and life and death in some contexts.
This attracted the retort: What delimiters are not "arbitrary"? The systems thinking response to that must be: those that have been reasoned.
By my reasoning, any scope here is too narrow if it does not include human identities immanent in the relationships immanent in information exchange, i.e. society. I would go further and say such a scope would be too narrow to even constitute systems thinking. (To avoid accusations of arrogance, I regard systems thinking as just another expertise that needs to be in the mix here alongside the technical talents that have gone into the technical wonders to date, and those other disciplines we’ve yet to engage.)
Our shorthand at AKASHA for these different scopes is to refer to the smaller as technological and the larger as sociotechnological, and it’s reassuring to see the Internet Policy Review journal reference our overarching conclusion in its glossary definition of SSI[8]:
Viewed atomistically, technologically, SSI looks quite sensible. At scale, as sociotechnology, the emergent consequences are malignant.
In pursuit of clarity of thought and communication, we categorize varying conceptualizations of identity as either noun-like, by which we mean enduring by design, and verb-like, recognizing that the human condition and human relations are never static. The bureaucratization of identity (e.g. legal identity) is noun-like. Your professional identity for example may be both (e.g. lifelong accreditation as certified by a professional body, and ever-evolving capabilities, understanding, performance, professional relationships, standing, etc.). Your identity as a parent is verb-like (beyond the comparatively trivial legal recognition of the fact).
Our conversations have highlighted a fundamental disconnect between our respective appreciations for the noun-like and verb-like categorisations, undetected until now.
Doc’s response is simply: “Credentials are nouns, but to present them is a verb.” However, our subject is the categorisation of conceptualisations of identity, not nouns and verbs in general. We have different ideas for what constitutes an appropriate level or depth of analysis.
Drummond has told me that both categories can be seen represented in Figure A of Appendix A of the Sovrin Glossary V3[9], as shown here. They cannot. Conceptualisations of human identity necessarily involve humans — their perceptions, their cognition, their behaviour, their relationships, their information exchange — and human society isn't visible in this technological schematic. The qualities distinguishing the noun-like and verb-like conceptualizations are manifest and felt only in the system in which the SSI technology would operate, never solely in the latter. To say society is represented because the blue box labelled “entity” could represent a human being would be as mistaken as saying the economy is represented in a diagram including a dollar sign, or a city’s traffic system reflected in a diagram with a box labelled "car".
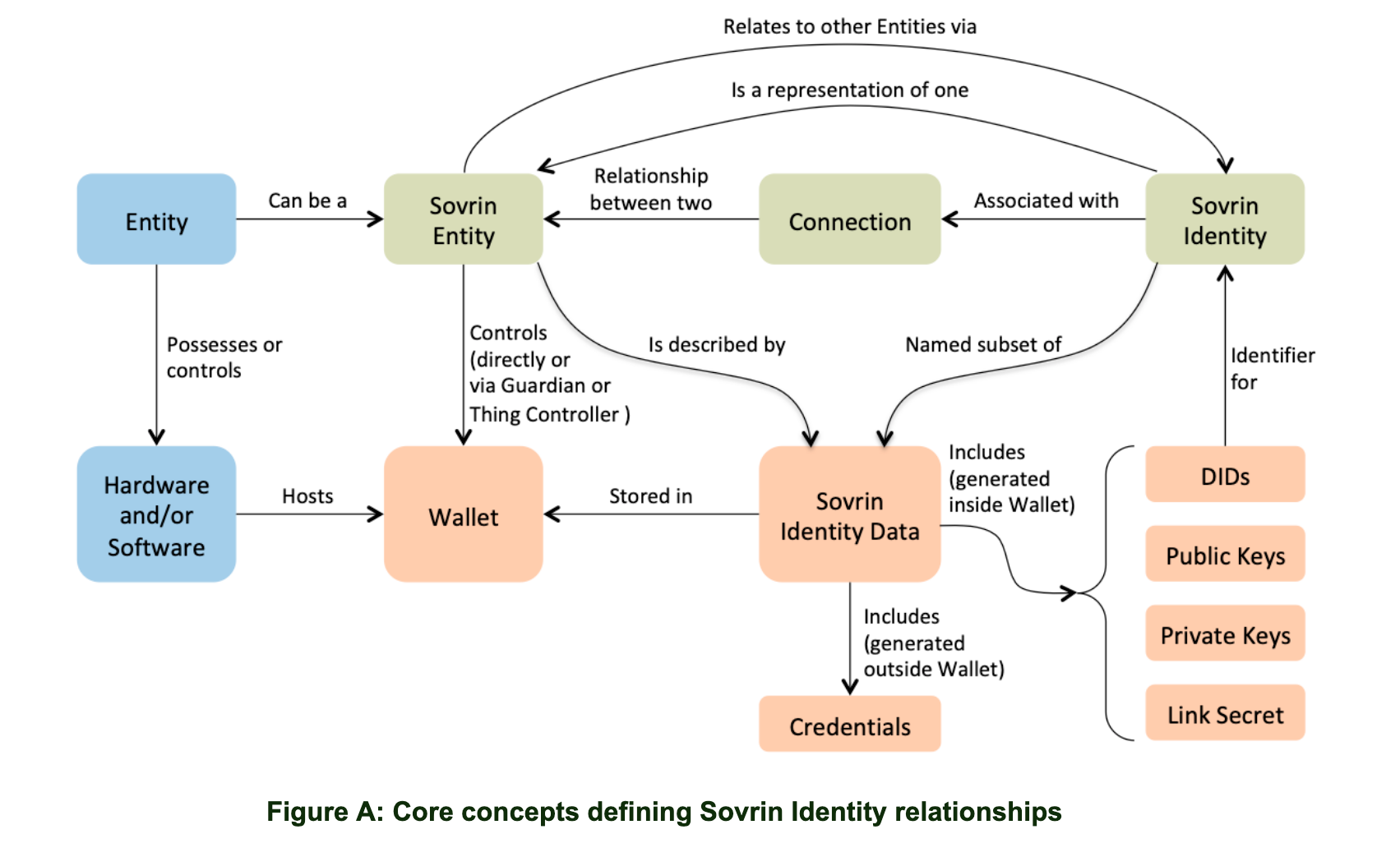
I may well have contributed to this confusion by not seeing the possibility for such confusion in the first place. The comparison table of SSI and generative identity that I developed at Doc’s apt prompt in 2019[10] does not distinguish the resultant qualities of the system in which the SSI system would operate from the latter alone clearly enough. Just as well I numbered the version 0.1!
The potential to make a difference in the world — agency — is integral to all conceptualizations of identity with which I am familiar; both noun-like and verb-like. I now appreciate however that there are quite different appreciations for agency, in my earlier conversation with Phil Windley as already documented and latterly with Doc.
While some try, I cannot consider agency to be something one can ascribe in isolation to an individual, especially if one is working in a design space aspiring, to a smaller or larger extent, to increase agency and/or perhaps help spread it around a bit more equitably.
Practically speaking, one may be said to have agency only alongside others similarly. It is embedded in and emanates from our social and cultural context. Intriguingly, “modern culture creates an agentic individual managing goals thought to reside in a personality or life course.” Thought to. However, any perception of “fully realized and unfettered actors pursuing their goals” is imagined[11]. But let’s break it down to make it more readily understood.
The capability to jump on a bike and get across town quicker than otherwise is agentic, and it’s easy to consider this as entirely personal agency. Nevertheless, this capacity is only realised because others conceived of the bicycle, designed it, manufactured it and the pavement, and perhaps taught you to ride it, etc. Your agency would soon be frustrated if others stopped making inner tubes. This agency would not for all practical purposes exist at all if it was unique to you for there would be no market for bikes and so no bike you could buy.
Being a speaker and a writer (assuming the attention of listeners and readers!) is agency realised, but only because your audience has similar communicative agency. Such agency is imbued because you are in fact doing what many others have the facility to do too (in this instance, communicating in a shared language).
Both identity and agency are social because they are deeply entwined. One cannot reliably work towards an agency-related purpose without appreciation for the interplay of all conceptualizations of identity, of both noun- and verb-like, and therefore such a goal remains unachievable without expanding one’s purview from the SSI system to the system in which the SSI technology system would operate.
Doc asks whether we should, effectively, invest time to turn each other around on this question, and I can’t deny the salience of the question. The way forward is to invite to our conversation, to our collaboration, those whose life’s work is understanding the manifestation and dynamics of agency.
According to Max Weber writing in 1920[12]:
The fully developed bureaucratic apparatus compares with other organizations exactly as does the machine with non-mechanical modes of production. Precision, speed, knowledge of the files, continuity, discretion, unity, strict subordination, reduction of friction and material and personal costs — these are raised to the optimum point ...
This acclamation of bureaucracy’s superiority may jolt the reader familiar with the more recent idea that bureaucracy is an undesirable and unviable form of organization. Nevertheless, it was a conclusion of its time and a perfectly rational one based on historical comparison. Unlike its forerunners, bureaucracy enforced equality and empowered citizens[13]. The advent of bureaucracy marked the comparative enhancement of agency in society. The individual now had official status — legal identity — and that status accrued rights over the ensuing decades. For this reason, one target of the Sustainable Development Goals is to ensure everyone has legal identity by 2030[14].
Drummond observes that the introduction of bureaucracy in the workplace wasn’t exactly so liberating, although one can dissociate bureaucracy from the dominant connotations of centralized and rigid organizational arrangements[15].
I disagree then with unqualified assertions along the lines that identity systems pre-dating SSI worked to subordinate agency to centralized or federated governmental systems operated by others. The bureaucratization of identity lifted agency up to the point where we only now find ourselves bumping uncomfortably against its ceiling. Moreover, the phrase “operated by others” may be recast as “by our own societies of which we each are a constituent.”
There’s a lot packed into this very brief mention of bureaucracy, many nuances beyond the scope of this post. In the simplest terms, I am no bald advocate of bureaucracy, but I believe that to cast its category aside is to taint the required systems thinking here, as we shall see below (see Governance).
I’m rapidly coming to the conclusion that the question of the atomistic self may be so integral to some people’s (cultural) identity that no length of conversation and no number of references[16] will sway let alone dispel a person’s belief that they stand apart, sovereign, perhaps in some extreme Ayn Randian opposition to extreme collectivism, present company excluded. One can moot that complex adaptive systems are very unlikely to entertain either extreme at any possible equilibrium, but there appears to be a psychological safety, perhaps a reassuring simplicity, in backing away as far as possible from the extreme one has learned to abhor, even if this leaves you appearing equally distant to many onlookers.
The question featured in conversation with Phil Windley (who compared natural human beings with artificial nation states to my surprise) and now with Doc too. My response to Phil is, I think, worth repeating here.
Drawing hard borders is your personal choice driven by one's own goals, context, values, and cultural lens. Drawing them makes no difference in the ecology of the whole ... as Gregory Bateson noted, they just form part of the very ecology they were supposed to delimit.
But drawing hard borders does make a difference when concreted in technical code from which Alice has no escape. Alice's context, values, and cultural situation differ from yours, and while you may sincerely hope for her to have "self-sovereignty" as you see it, your architectural imposition actually denies her it.”
The very last sentence should be elaborated.
The community that has designed SSI is comparatively and unarguably homogeneous — in disciplinary terms, in gender terms, in professional terms, and in its cultural context. It has then done, as Conway's law[17] hints, only what it could do — render its own contextual understanding of what constitutes "digital trust" and "digital identity" and "agency" and "human relations" into code; more specifically technical protocol. Tight protocol. Not a plurality of protocols. Not a wide variety of schema. But prescriptive protocol. It is not difficult to contemplate that perhaps other people in other communities in other contexts, perhaps a high-trust society for example, ‘see’ things or ‘feel’ things differently and may wish to subscribe to alternative protocol if only there was a choice.
But back to borders.
I have found no modern day paper concluding that any person has a mind entirely ‘their own’. A (biological) brain, yes. A (informational) mind, no.
However you approach the topic — from anthropology to information theory to psychology to theology — the phenomenon of distributed cognition is widely accepted or at least strongly hinted at. Some SSI architects and developers may perceive hard borders, they may have inherited language that propagates atavistic perceptions (and other cultures / languages very much less so, if not entirely to the contrary), but that doesn't mean such hard borders exist.
Fortunately, Drummond tells me there is no atomistic self in any SSI architecture — only decentralized identifiers (DIDs), relationships, verifiable credentials (VCs), and governance frameworks. This is most uncharacteristic of the conversations I’ve had with those working in this domain, and contradicts core messages across many websites and blog posts dedicated to SSI and related matters, especially “solutions”, but personally I find it a deep relief to hear him conclude as much. I’ve encouraged him to write on the matter.
Doc and I both dislike claims by SSI architects to be building the “identity layer”, a layer of the Internet that has been missing for the past half century, or so we are told.
For my part, as mentioned in the SSI dystopia critique but also I hope evident from this blog post alone, I cannot possibly conceive of human identity ‘living’ alongside TCP/IP, UDP, and HTTP[18]. Having already presented human identity as an environmentally-distributed and relational construct rather than merely a psychological or biological phenomenon[19], I have no problem at all with the digital augmentation or extension of the human being. On the contrary, given the challenges our species faces this century, this collective agency will likely prove essential[20].
Norbert Wiener anticipated this informational, cyber extension of ourselves way back in 1950[21]. Seventy years later it seems almost timid to define the individual here as an assemblage of the biological, psychological, informational, and interfacial. Nevertheless, such a cyborg entails the addition of ‘the digital’ to the biological and psychological, not the substitution of the former for the latter. The turn of phrase “identity layer” pertains only to the digital fabric and so can never constitute human identity of itself in just the same way HTTP isn’t called “the conversation layer” and the FOAF ontology[22] isn’t called “the human relations layer”.
One would think such an observation would be wholly compatible with beliefs regarding the individual’s autonomy, her sovereignty. Alice proxying her identity to a layer of a global information network is more Borg[23] than self-sovereign! (See Trust triangles below.)
The defense may be that it’s only words, but words play a role in the formation of mental models, mental models play a role in our shaping of our tools, and our tools then shape us[24].
Talking of words — let’s talk about trust.
When Alice and Bob trust each other, they make themselves vulnerable to each other. There remains some chance that one’s faith in the other will turn out to be misplaced for whatever reason.
No-one needs to trust that gravity will keep their feet pinned to the planet, or that 2+2=4, because “trust as a concept has no meaning in a fully deterministic setting.”[25] Rather than enshrining trust in code, cryptographic techniques eliminate the need for trust in the first place. This has some advantages in some contexts, but those advantages must be qualified given that trust is integral to the formation of human relationships and the fabric of human society.
Ultimately, “trust may be thought of as a functional prerequisite for the possibility of society in that the only alternative to appropriate trust are ‘chaos and paralysing fear’.”[26] Some may proffer cryptographic digital processes as a way out of this dichotomy, except you can’t rip out a fundamental social process and still expect the same quality of human relations, of community.
We have a choice. At AKASHA, we frame our work in terms of setting out to combine the best of Web 3[27] wizardry and the best of human nature, relying on the latter where we can and as we should, and crafting the former as and when scale demands. Independent ethics panels will help determine the contextually appropriate blend.
Triangles are to be found everywhere there is a need for structural rigidity — e.g. the Manhattan Bridge, the Eiffel Tower, bicycle frames — and similarly ‘trust triangles’ achieve informational rigidity with informational triangles. This is the kind of outcome those in the West decry of China’s nascent identity and social credit system. One might congratulate them at least for recognising and being clear about what they’re building.
This paragraph from the SSI dystopia critique caused Drummond to question if I was equating any form of a trust triangle with the abuses of a social credit scoring system? After all, trust triangles have existed for as long as human community.
Non-digitalized trust triangles have existed for millennia, and that is a core part of my thesis. The problem is when you digitalize them indiscriminately.
Historically nuanced claims (“I would have graduated had my parents not died suddenly”) become stiflingly binary (“I cannot verify that I graduated because I did not graduate”). One's psychological framing / narrative selves are severely inhibited (“I cannot claim I nearly graduated”, and so the self narrative becomes “I failed to graduate”). One's 'wriggle room' is vanished. The architecture SSI sets up is designed to spread and envelop many aspects of every relationship, and one is locked rigid into a set of triangular potentials. It lends a new meaning to being triangulated.
Drummond considers SSI “the most contextually-sensitive identity technology I know of” in contrast to my assertion that “SSI cannot communicate context.” You won’t be surprised to learn that we’re both right ... in our different contexts.
Drummond’s context is identity technology, whereas mine is human beings and nature. SSI may be the most contextually-sensitive technology, but what it sets out to do contextually is an utterly miserable substitute for contextually-sensitive non-technologized human relations.
Reflection on the inevitable nuances prompted Drummond to ask, in effect, whether such concerns should impair the majority’s facility to offer verifiable claims. It’s a good question, one the SSI community, SSI vendors, and all parties looking to support a roll-out should ask of their respective ethics committees.
In the SSI dystopia critique[28] I point to the deeply undesirable outcomes of social media behaviours that went largely unpredicted just a decade ago, and I begin the process of anticipating similarly poor outcomes of SSI in common use in the years to come. I claim:
There is no known way to constrain SSI from enabling if not catalyzing these applications. Such constraints might require a friction or a frustration of interoperability entirely counter to the architectural and engineering goals.
I go on to highlight the way in which SSI effects the societal regulators of social norms, legal code, and technical code[29]:
SSI fundamentally changes the balance of these regulators in the context of identity. It diminishes the role of legal code and has software code and social norms supervene.
Drummond has good cause to push back. And I think I have good reason to push back his push back. Most importantly, this debate goes to the heart of the matter — to the woeful inadequacy of SSI principles, in all their variety both past and present, and to the urgent need to corral multidisciplinary systems thinking to make the very best of the progress that has been made to date.
Drummond points to the working group at TNO in the Netherlands focused on governance and constraints, specifically its focus on the prevention of coercive bad actors[30]. And he quite rightly champions the ToIP [Trust over IP] stack[31]. While we can argue about the validity of the T in ToIP, “it combines both cryptographic trust at the machine layer and human trust at the business, legal, and social layers.” He notes:
... providing the proper frictions is a key focus of most of the SSI ecosystem governance frameworks in which I am involved. It's just that it can now be intentional friction instead of unintentional friction.
I do like the use of (un)intentional there.
The TNO working group is indeed an example of stakeholders seeking to reintroduce necessary friction. TNO is not the first to frame coercion in terms of the "800-pound gorilla", but that's not the sole source of coercion, and coercion is not the only social mechanism in play. While most welcome, there can be little doubt by any reading that this runs counter to the founding architectural and engineering goals of SSI.
I'm not saying I disagree with some of the ideas that parties such as TNO have developed. I'm saying that they too are effectively recognising SSI's innate ill-effects and are trying to head them off at the pass.
Similarly, I see the ToIP undertaking as recognition of the invalidity of any justification of SSI in terms of right-libertarianism or negative liberty. By affecting what some would call “removing choice”, it runs counter to the clarion call of "self-sovereignty".
And here we briefly revisit bureaucracy.
One can list the qualities of the bureau (office) in terms of being formalized, specialized, standardized, rule-based, and impersonal. Similarly, bureaucracy implies a normative and authoritative structure considered to be both rational and legitimate[32]. I imagine I’m not alone in considering these qualities perfectly suited to the proper administration of the ToIP governance stack. I could contemplate participating in a B2C relationship subject to such good governance, on the basis that doing so didn’t contribute to its wider adoption outside the domain of such good governance. However ...
The ToIP undertaking is necessary but insufficient. Failure to participate in the governance side of the stack, however the requisite participation may be prescribed, does not preclude participation in the technical side of the stack, especially by the very actors from whom we can perhaps expect the most harmful emergent outcomes in their natural inclination towards self-interest over system-interest in the absence of good corporate governance; you, me, and our friends and family in peer-to-peer information exchange.
As typified by TNO's conclusion, the only constraint is to reverse out of the ubiquitous meme that SSI is just like a wallet with credentials in it that you can pull out and present at any time as you wish.
Longer-term, one must also question the sustainability of ToIP. SSI protocols typify a set of technologies that radically erode Coase’s costs of using the pricing mechanism, better known as transaction costs[33]. As such costs constitute the Coasian explanation for the very existence of “the firm”, the SSI technology stack first enables the fragmentation of any value chain beyond the governance domain of any one or small set of organizations, and ultimately threatens the very existence of the organizations it calls upon to govern it.
It's time we accept SSI for what it was. Unrealistic. Where's the "self-sovereignty" in being subject to these bureaucratic algorithms? The term "self-sovereign" is not just inappropriate, it's beginning to undermine the efforts of its evangelists. It's a label associated with an ethos and set of design principles that hinders rather than helps anyone now, that simply fails to live up to the requisite complexity. It does an injustice to the potential applications of the protocols developed in its name.
I believe we're just beginning to get real about the natural complexity of human identities immanent in relationships immanent in information exchange. Currently, this involves the existing ‘digital identity’ community making some well-meaning attempts to identify specific problems and gaps and fix and fill them respectively. Yet if we are to deliver in contexts rarely even mentioned to date[34] — psychological, sociological, and ecological health — I believe a deeper multidisciplinary review is necessary.
Steps to an Ecology of Mind: Collected Essays in Anthropology, Psychiatry, Evolution, and Epistemology. Gregory Bateson. 1972. University of Chicago Press. ↩︎
A simpler way. Margaret Wheatley and Myron Kellner-Rogers. 1998. San Francisco, CA: Berrett-Koehler Publishers. ↩︎
The Narrative Self. Marya Schechtman. In The Oxford Handbook of the Self, edited by Shaun Gallagher. 2011. Oxford University Press. ↩︎
SuperCooperators: Altruism, Evolution, and Why We Need Each Other to Succeed. Nowak, M., Highfield, R., 2011. Simon and Schuster. ↩︎
General Systems Theory: Foundations, Developments, Applications. Bertalanffy. 1967. George Braziller Inc. ↩︎
The Systems View of Life: A Unifying Vision. Capra & Luisi. 2014. Cambridge University Press. ↩︎
https://cyber.harvard.edu/lists/arc/projectvrm/2020-01/msg00020.html ↩︎
https://policyreview.info/glossary#node-1524 Retrieved 26 February 2021 ↩︎
Appendix A: Sovrin Entities, Identities, and Connections, Sovrin Glossary v3, December 2019 https://docs.google.com/document/d/1gfIz5TT0cNp2kxGMLFXr19x1uoZsruUe_0glHst2fZ8/edit# ↩︎
A call for interdisciplinarity — generative identity and the Internet Identity Workshop, Philip Sheldrake, September 2019 https://akasha.org/blog/2019/09/30/a-call-for-interdisciplinarity-generative-identity-and-the-internet-identity-workshop ↩︎
The “Actors” of Modern Society: The Cultural Construction of Social Agency. Meyer and Jepperson, 2000. Sociological Theory 18, 100–120. https://doi.org/10.1111/0735-2751.00090 ↩︎
In Economy and society. 1978. Roth and Wittich, eds. Berkeley: University of California Press. ↩︎
Maybe it is time to rediscover bureaucracy. Olsen. Journal of public administration research and theory. January 2006. http://faculty.cbpp.uaa.alaska.edu/afgjp/padm610/Maybe%20It's%20Time%20to%20Rediscover%20Bureaucracy.pdf ↩︎
See: The Sustainable Development Goals, Identity, and Privacy: Does their implementation risk human rights? Privacy International. 2018. https://privacyinternational.org/long-read/2237/sustainable-development-goals-identity-and-privacy-does-their-implementation-risk ↩︎
Work, Human Agency and Organizational Forms: An Anatomy of Fragmentation. Jannis Kallinikos. Organization Studies, 2003. https://journals.sagepub.com/doi/pdf/10.1177/0170840603024004005 ↩︎
For example: The Cognitive Ecology of the Internet, Smart, Heersmink, Clowes, 2017. in: Cowley, Vallée-Tourangeau (Eds.), Cognition Beyond the Brain. Springer International Publishing, Cham, pp. 251–282. https://eprints.soton.ac.uk/397486/1/cognitive_ecology_internet.pdf ↩︎
See https://en.wikipedia.org/wiki/Internet_protocol_suite ↩︎
Distributed selves: personal identity and extended memory systems. Heersmink. 2016. Synthese. https://www.researchgate.net/publication/301691846_Distributed_Selves_Personal_Identity_and_Extended_Memory_Systems ↩︎
See https://akasha.org/blog/2020/07/24/cooperating-at-scale-part-one ↩︎
The Human Use Of Human Beings: Cybernetics And Society. Norbert Wiener. 1950. Houghton Mifflin. ↩︎
Trust in Society. Karen Cook, ed. Russell Sage Foundation, 2001. ↩︎
Trust as a Social Reality. Lewis and Weigert. Social Forces 63, no. 4 (1 June 1985): 967–85. https://doi.org/10.1093/sf/63.4.967, quoting: Trust and Power. Luhmann. John Wiley & Sons, 2018. ↩︎
An information network emerging from and made possible by new cryptographic techniques. ↩︎
Under the heading “We swipe therefore we are” ↩︎
Under the heading “All in the mix” ↩︎
See the subsection "countermeasures to coercion" https://github.com/hyperledger/aries-rfcs/blob/master/concepts/0289-toip-stack/README.md#countermeasures-against-coercion ↩︎
Ibid. 13 (Maybe it is time) ↩︎
It is reassuring to see the formation of the ToIP Human Experience Working Group during the second half of 2020. ↩︎