Reusable KYC: when a dedication to decentralization self-sabotages
Are we our own worst enemy?

Are we our own worst enemy?

Aldous Huxley (1937) regarded the decentralization of industry and government necessary for a better society. Norbert Wiener’s insights (1950) into the dynamics and ethics of humans and large computer systems hinted at the advantages. Marshall McLuhan (1962) anticipated a shift from the centralized mechanical age to the decentralized electronic age, coining the term global village as shorthand for such a welcome outcome. E.F. Schumacher (1973) considered decentralization allied with freedom and one of “the truths revealed by nature’s living processes”. Steven Levy’s hacker ethic (1984) includes the tenet “mistrust authority – promote decentralization”. And Nicholas Negroponte (1995) regards decentralization as one of the four cardinal virtues of the information society (alongside globalization, harmonization and empowerment).
I wrote that paragraph 👆🏼 in 2018. I first wrote about Decentralized Autonomous Organizations in 2014 and received a call that June from a nascent project going by the name Ethereum. And I have been somewhat obsessed with the potential of decentralized and distributed systems since learning about the key design influences and considerations that shaped the development of the Internet (late-60s) and the Web (late-80s) way back in the day.
I make this clear because what I'm about to say can be mistaken for a reluctance to decentralize. Or a dissatisfaction with decentralization. It is neither. It is a caution about attempts to decentralize in ways that undermine common purposes of decentralizing.
We know decentralization is a means and not an end in itself (Schneider 2019). We know that some forms of decentralizing in some contexts may be compatible with desirable goals expressed in such terms as prosocial and human flourishing. We also know that other forms in other contexts might produce undesirable outcomes and my focus right here is such an exemplar, so-called reusable KYC.
KYC stands for Know Your Customer. Financial institutions must confirm your legal identity to a certain level of confidence to satisfy regulators intent on preventing money laundering, i.e. where illegally obtained money is made to appear legitimate. KYC is needed in finance contexts such as opening a bank account, investor accreditation, and web3 fiat on- and off-ramping.
Chainalysis reports illicit ledger addresses sent $22.2 billion worth of cryptocurrency last year, up on 2021 but down from the high of $31.5bn in 2022. By way of a fiat comparison, one money laundering network laundered $4.2bn through HSBC between 2014 and 2017. It was unearthed by an independent monitoring team "installed by the US Department of Justice (DoJ) as part of a deal not to prosecute HSBC in 2012, when the bank admitted allowing Latin American drug cartels to launder hundreds of millions of dollars through its accounts."

I don't want criminals to think they can profit so easily from their crimes. If KYC frustrates money laundering, then that's a plus. If it has negative consequences in the contexts of the functions that money performs in society — and recall that cash payments are anonymous — then that's something that warrants continued research and action, but that's not an area of expertise I can claim. My research is useful when it comes to the consequences it might have in other contexts, specifically the contexts of identity and system health more broadly.
Consider the question “Who are you really?” And by corollary, “Do you know who you are really dealing with?”
As with all writing and dialogue, these questions come laden with contexts, both historic and contemporary, i.e. appreciation for when such questions may typically arise and the immediate circumstances in which they are invoked.
If I rephrase the question with the goal of discarding some of those connotations, it might be: “Who are you to whom in a given context?”
When it comes to legal identity, the whom is the nation state and corporations adhering to that state’s KYC laws, and the context is making you legible for such bureaucratic purposes. Importantly, it is no more ‘who you really are’ than loving daughter or loyal friend, great cook or fanatical cyclist, trusted family doctor or slightly eccentric neighbour.
Relationships matter. All variety of contexts matter. And legal identity too easily rides roughshod over both, especially when supercharged by software designed with less than appropriate diligence.
Web3 websites and slidestacks and memes leave you in no doubt — we want to explore other ways to organize society that might at a minimum be less inequitable, less bureaucratic, and less damaging to the web of life of which we are part. I'm up for that.
So where does this leave 'reusable KYC'?
Reusable KYC may well be highly prized in such tightly constrained contexts as anti-money laundering and investor accreditation procedures, but it's also a pollutant beyond such contexts. And it gets worse. In light of the shared bureaucratic heritage of both KYC processes and the concepts underpinning computer science, the pollutant finds itself quite at home in its new environment, spreading readily. Let me try and explain its polluting qualities.
From experience, too many technologists subscribe to the neoliberal fallacy of individual choice and control. Would anyone share sexually explicit digital photos and videos that could be used against them? No! But of course they do. Would anyone sign up to these egregiously invasive terms and conditions? No! But of course they do. Would anyone keep using social media to the point they cannot concentrate on more important things? No! But sadly. In short then, as for all digital innovations, all parties involved in reusable KYC will inevitably do things that its current advocates either haven't thought about or don't wish to bring to anyone's attention.
This kinda indicates that those advocates are some blend of negligent and dishonest, but let's give them the benefit of the doubt. Let's assume they have given it some thought and came to the conclusion that their cryptographic magic has everything covered.
It does not. They are wrong.
Do not confuse information security techniques for some ultimate defense against poor systemic outcomes.
Perhaps enchanted by the fact that the absolute minimal information is imparted as a consequence of their work, our protagonists here crack on working their new found techniques into all variety of life's interactions. But as systems exhibit qualities that cannot be traced to the nature of a single interaction, systems thinking requires consideration of the system as a series of relationships and as a whole. Let's do a bit of that now.
Verifiers: Would anyone ask for KYC credentials when doing so would be considered by anyone investing a few minutes thinking about it as overkill for the application at hand? Yes. It's so easy. If it might help the verifier's business in some way, what's the harm?!
Presenters: Would anyone present KYC credentials when asked in the moment, even when it's unrelated to any regulatory imperative? Yes. I mean it only takes a click. If it helps them get what they want right now, what's the harm?! In fact, they should just set this up programmatically ... again, what's the harm?!
Issuers: Having figured out provision of the reusable KYC credential, would anyone consider offering verifiable credentials for the various separable information gathered during the KYC determination? Age? Sex? Nationality? Wealth? Yes! If it's what the customer wants, if it's what the businesses in their lives want, then what's the harm?
And of course there is no harm for each of these example actions ... in isolation. On the contrary. And that's the point here. The actors involved cannot be criticized for being unable to answer 'what's the harm?' at the systemic level, or even for failing to ask the question at all. The responsibility lies squarely with the system architects. It is a professional and ethical obligation (see Live or Die).
When the outcome of a KYC process is made reusable without ongoing governance constraining its use and application, it will be used and applied in ways that make it a pollutant at the system level, which by definition has very poor social outcomes for system participants. How does this happen?
I describe such concerns more broadly and in more detail in Human identity: the number one challenge in computer science, but it's always a good idea to find different words to describe more specific aspects in the never-ending pursuit of effective communication. So how does this read? ...
You don't need legal identity for the vast majority of social interactions in your neighbourhood, at work, down the gym, or even online, etc. Human identities (by which I mean not legal identities, not bureaucratic identities) are in the eyes of the beholders. You mean different things to different people in different contexts. Human identity is a set of never-ending dynamic processes that helps each of us figure out what everyone else means to us in varying circumstances, and indeed we 'show up' differently according to our own current expectations and our appreciation for others' expectations and the corresponding social norms. We rely on recognizing someone again socially and contextually and most definitely not via some comparatively abstract bureaucratic tabulation. The corresponding skills are innate and integral to our outstanding evolutionary success as cooperators.
Quite naturally then we carried this into digital life. The vast majority of readers here will have or have had multiple email addresses and profiles and handles and avatars and social groups and channels. It's a personal and social freedom. A beautiful complex, entirely compatible with and necessary for those web3 hopes and dreams I noted earlier. And while we're at it, it's wholly compatible with the sentiments of A Declaration of the Independence of Cyberspace (even if its sentiments perhaps stretch a little too far in light of more recent insights into the qualities of a healthy digital fabric in our lives).
Now I need your imagination.
Imagine that the behaviours I describe above for verifiers, presenters, and issuers play out — they each make sense in the moment after all. Very few of these actors, bordering on absolutely none of them, give any time to considering the emergent consequences of their role in the big scheme of things in much the same way we all say "I'm stuck in traffic" rather than "I am traffic."
The encroachment is slow at first, too negligible for the poor social outcomes to be apparent. We all crack on. We all behave in ways that serve our self-interest in the moment and emulate those who have already done so. The credentials are used in previously unimagined ways and participation is compelled when the only alternative is exclusion.
Some bright spark for example suggests that reusable KYC could be useful in terms of securing widespread Sybil resistance (ensuring every account is human and every human is represented only once in the system) forgetting that Sybil was a human. She/they may have been an extreme example, but we are all Sybils. It's our nature. It's a psychological and sociological imperative. If we cannot secure well-governed Sybil resistance tightly constrained to those very few contexts where corporeality matters (e.g. wealth distribution and democratic process), it's far far preferable to live without such a mechanism at all than to have it loom large over everything.
There's a governance theme emerging here don't you think.
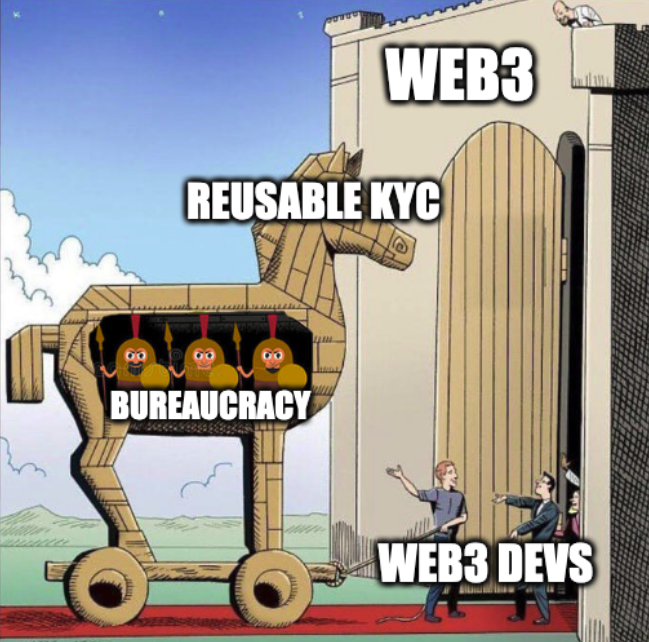
In just the same way that everyone piled on Facebook without personal responsibility for the significant societal downsides of such authoritarian surveillant homogeneity, bureaucratic identity and KYC process contaminates the web3 ecology and so then the accompanying hopes and dreams. In setting out to leave the machinations of nation state bureaucracy and the old financial system behind as much as we might without giving criminals a free pass, instead of designing for psychological, sociological, and ecological health in digitally mediating and augmenting human identity, we recreated the rigid old system on digital steroids by accident.
Not only did we welcome the Trojan horse in, we designed and built it ourselves.
Note: A 2000-word blog post is ill-suited for giving the critical concepts here the attention they deserve. As suggested in the post, please refer to Human identity: the number one challenge in computer science for a deeper analysis.